
Outwit Electronic Snoopers
by John E. Cunningham
(Radio-Electronics February 1972)
The electronic snooper will resort to anything to listen to your conversations. See how to plug his electronic ears.
"Bugging" or electronic eavesdropping, which was something strictly from science fiction, is a big business in the United States today. You don't hear much about it, because legitimate manufacturers of such devices promote their products primarily to law-enforcement agencies, and makers of illicit bugs prefer to attract as little attention as possible to their operations.
FCC regulations prohibit the sale or use of unauthorized eavesdropping devices, but the fact is that a reasonably effective bug is relatively easy to build. They usually can be readily concealed, and since their signals can only be picked up over a distance of a few hundred feet at the most, it is almost impossible to enforce the regulations.
Bugs have been used by private detectives to gather information for their clients, by employers to eavesdrop on their employees, by businessmen to gain access to their competitor's secrets, and by jealous husbands to check on their wives. In fact, bugs are so easily built or purchased that it is safe to assume that anyone's conversation may be bugged if a person feels it is worth the risk.
This widespread use of eavesdropping devices has led to the development of a new profession-that of the electronic "debugging" expert. Many security consultants spend full time locating bugs and providing secure areas for private business discussions. Furthermore, many electronics technicians are being called in by companies to assure that their secrets are not leaking out to competitors by way of bugs which have been secreted on their premises.
There are four types of electronic eavesdropping devices that are in common use today:
- High-gain directional microphones.
- Hidden microphone wired directly to a listening or recording device.
- Miniature radio transmitters.
- Bugs used in connection with telephones.
 The first type, the high-gain directional microphone, is the easiest to defend against. It is simply a microphone equipped with a parabolic reflector to make it highly directional. Devices of this sort are large and hard to conceal. Usually, they cannot pick up conversations at distances of more than about 150 feet. The defense is simply to hold conversations in areas with reasonably soundproof walls and closed windows. It also helps to have a distracting source of sound, such as a transistor radio in the room.
The first type, the high-gain directional microphone, is the easiest to defend against. It is simply a microphone equipped with a parabolic reflector to make it highly directional. Devices of this sort are large and hard to conceal. Usually, they cannot pick up conversations at distances of more than about 150 feet. The defense is simply to hold conversations in areas with reasonably soundproof walls and closed windows. It also helps to have a distracting source of sound, such as a transistor radio in the room.
The second type is a microphone that is hidden in a room and connected by wires to a remote point where the eavesdropper listens with an amplifier and headphones, or has planted a tape recorder. This type is usually difficult to track down because it doesn't radiate.
By far the most common type of bug is the miniature radio transmitter such as the one shown in Fig. 1. This device is actually a battery-operated transmitter. The eavesdropper merely plants it and then picks up its signal from some convenient place where he is not apt to be noticed.
The fourth, and probably most sophisticated type of bug is the telephone bug. Many different types of telephone bugs are in use. They range from simple wiretaps to radio transmitters hidden in the telephone. The later are often arranged to draw power from the telephone line and use the telephone transmitter as a microphone.
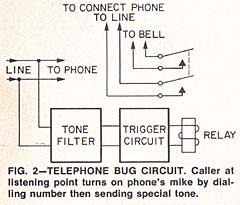 A very sophisticated telephone bug, shown in Fig. 2, effectively "answers" the phone before it rings. In this circuit, a tone-operated relay is connected so when a tone of the proper frequency is transmitted on the line. Once this kind of bug is installed in the victim's phone, the eavesdropper can dial the number from any other phone in the United States. There is a short period of time between the instant that the connection is made and when the bell starts to ring. During this interval, the eavesdropper transmits a tone over the line with a small portable oscillator. The tone prevents the bell from ringing and connects the victim's telephone to the line. The eavesdropper can then listen to all the conversation in the room from as great a distance as he wishes. The only way that the victim might become aware of the bug is when he fails to get a dial tone when placing a call. Even this usually isn't noticed, because when the eavesdropper hears someone attempting to use the phone he can quickly hang up.
A very sophisticated telephone bug, shown in Fig. 2, effectively "answers" the phone before it rings. In this circuit, a tone-operated relay is connected so when a tone of the proper frequency is transmitted on the line. Once this kind of bug is installed in the victim's phone, the eavesdropper can dial the number from any other phone in the United States. There is a short period of time between the instant that the connection is made and when the bell starts to ring. During this interval, the eavesdropper transmits a tone over the line with a small portable oscillator. The tone prevents the bell from ringing and connects the victim's telephone to the line. The eavesdropper can then listen to all the conversation in the room from as great a distance as he wishes. The only way that the victim might become aware of the bug is when he fails to get a dial tone when placing a call. Even this usually isn't noticed, because when the eavesdropper hears someone attempting to use the phone he can quickly hang up.
This type of bug is complicated and expensive, but it has the advantage that once the bug is planted, the eavesdropper can listen in almost complete safety, to everything that is taking place.
Debugging techniques
When an electronics technician is called in to locate a bug or to provide an electronically secure area for private conversations, he must use every bit of ingenuity at his command. The state-of-the-art at the present time seems to be on the side of the eavesdropper.
The first step in debugging a room is to conduct a painstaking and thorough physical search of the premises. This is time consuming, but is usually well worthwhile. Many experts charge fees of up to $1,000 to assure that a conference room is secure.
When conducting a search, pay particular attention to anything that is new, or temporarily present in the room. A favorite way of temporarily planting a bug is to conceal it in an item of personal property that can be left as though by accident. Thus a competitor's representative may leave a briefcase, raincoat, or umbrella containing a bug during a visit to a facility. Many modern bugs are inexpensive and are considered expendable. Sometimes bugs are concealed in gifts such as pictures.
An important factor in debugging an area is the fact that a professional agent rarely plants only one bug. He plants at least two and sometimes more. So if the technician locates a single bug, he should not consider his job done. The bug that he found may have been deliberately planted in a place where it would be easily found to lull the victim into a false sense of security, while another bug is transmitting all of his conversations.
 A small metal locator of the type used to locate buried objects is a valuable aid in locating wired microphones that do not radiate.
A small metal locator of the type used to locate buried objects is a valuable aid in locating wired microphones that do not radiate.
When a conference room is first built, or at a time that it is known to be secure, make a "map" with the aid of a metal locator showing the location and size of metallic objects. If during a subsequent search with a metal locator, new metal objects are detected in the walls, ceiling, floor, or furniture, further investigation is warranted. If no new metal objects are located, carefully inspect existing ones such as lamps, vases, and electrical outlets.
RF field-strength measurements
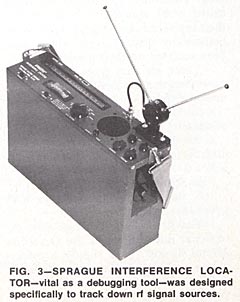
Most miniature-transmitter type bugs can be located with RF field-strength measurements. A typical interference locator that has been very effective in locating clandestine transmitters is shown in Fig. 3. The search is often simplified by first carefully examining all signals on frequencies that the eavesdropper is apt to use. The professional will never use a frequency where his bug is likely to be picked up by other users of the spectrum. One bug was located because it was interfering with air traffic communications. Frequencies are usually selected where sensitive receivers are readily available commercially. This factor, together with the fact that short antennas are efficient, has led to a tremendous number of bugs operating in and just outside of the standard FM band of 88 to 108 MHz. Commonly used eavesdropping frequencies are listed in Table 1.
Amateur eavesdroppers are apt not to be as aware as the professional of the risk of using certain frequencies. They use almost any frequency where they can build small efficient transmitters. This means almost any frequency up to about 200 MHz might be used. The search isn't complete until the entire spectrum has been checked.
 Make debugging field-strength measurements by carefully identifying each signal that is picked up in the suspected area. Many bugs use voice-operated relays that turn the bug on only when a conversation is taking place. For this reason, the searcher should talk continuously while making the measurements. Otherwise, the bug might not be radiating while a measurement is made. While making measurements, if the investigator hears his own voice over the field-strength meter, it is a sure sign that a bug is operating in the vicinity.
Make debugging field-strength measurements by carefully identifying each signal that is picked up in the suspected area. Many bugs use voice-operated relays that turn the bug on only when a conversation is taking place. For this reason, the searcher should talk continuously while making the measurements. Otherwise, the bug might not be radiating while a measurement is made. While making measurements, if the investigator hears his own voice over the field-strength meter, it is a sure sign that a bug is operating in the vicinity.
Another popular debugging meter, called the "hound dog" is shown in Fig. 4. This unit is not tuned, but has a broad response to signals from below the Citizens band to above the FM band. Since the majority of bugs operate in or near the standard FM broadcast band, the meter is made most sensitive over this part of the spectrum.
The meter is used to probe the walls, floors, and ceiling of the suspected area, as well as all objects in the area. Its sensitivity is adjusted to provide a minimum reading on signals from local FM and TV stations. When it is brought in close proximity to a bug, the meter indication will rise sharply. This simple meter in the hands of an expert will detect almost any bug of the radio transmitter type.
In areas where there are many strong signals, it is often advisable to make the search after 2 AM when most stations are off the air.
Telephone debugging
 Because of the possibility of wiretapping, a telephone should never be considered completely secure. The phone itself, however, can be debugged. Begin with a thorough search inside the phone for foreign objects. Then make field-strength measurements to detect any transmitter that wasn't discovered by the physical search.
Because of the possibility of wiretapping, a telephone should never be considered completely secure. The phone itself, however, can be debugged. Begin with a thorough search inside the phone for foreign objects. Then make field-strength measurements to detect any transmitter that wasn't discovered by the physical search.
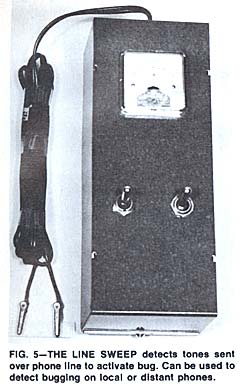
Tone-operated telephone bugs can be detected with an instrument called the "Line Sweep", shown in Fig. 5. This device is connected to the telephone line and, as its name implies, generates a tone which is swept through the audio spectrum while a meter monitors the line voltage. The voltage on the phone line is normally approximately 50 volts. If while the line is being swept, the polarity of the voltage reverses, it means there is an incoming call.
If while the instrument is sweeping the spectrum, there is a significant dip in the line voltage, there is probably a tone-operated bug on the line. More often than not it will be in the phone itself, but it could be anywhere along the line. Once you know there is a bug, it is simply a matter of diligent searching to find it.
The Line Sweep can also be used to check any local or distant phone for the presence of a tone-operated bug. Simply advise the party on the other end not to answer his phone and then dial his number. Immediately after the number is dialed, turn on the sweep. After a few seconds of sweeping the line, the ringing sound will stop if a bug is connected to the line.
 Automobiles aren't always safe
Automobiles aren't always safe
It is quite easy to bug an automobile. There are plenty of places to hide the bug, and the battery will supply plenty of power to operate a bug that will have a considerable range. The antenna can be passed through a small hole in the body, or in some instances the auto radio antenna has been used.
The proper way to search for a bug in an automobile requires two people-one inside talking continuously to trigger any voice-operated device and the other outside making field strength measurements.
Countermeasures
 Perhaps the biggest question is not locating the bug, but taking the proper action to restore security. The electronics technician has completed his job when he has either located every bug in an area, or assured himself that there are none. If a bug is discovered, it is up to the proper security authorities to decide what action to take. One common approach, once a bug is located, is to leave it undisturbed, hoping to mislead the eavesdropper with false information. The technician should always check with his client before taking any action.
Perhaps the biggest question is not locating the bug, but taking the proper action to restore security. The electronics technician has completed his job when he has either located every bug in an area, or assured himself that there are none. If a bug is discovered, it is up to the proper security authorities to decide what action to take. One common approach, once a bug is located, is to leave it undisturbed, hoping to mislead the eavesdropper with false information. The technician should always check with his client before taking any action.
The names and addresses of manufacturers of debugging equipment are given in Table 2, and further information may be found in the following books:
Security Electronics by J.E. Cunningham, Howard W. Sams
Business Intelligence and Espionage by Richard M. Greene,
Dow-Jones Irwin, Inc. Homewood, Ill.
| TABLE 1 |
TABLE 2 |
| Frequencies commonly used for bugging
|
Manufacturers of Debugging Equipment |
60 - 88 megahertz
88 - 108 megahertz
108 - 110 megahertz
27 - 28.4 megahertz
|
Sprague Electric Company, North Adams, Mass-Model 600
R.B. Clifton, 11500-W N.W. 7th Ave., Miami, Fla.-Hound Dog and Line Sweep
|
|

|
|



