| Home | Info | About Us | FAQ | Contact Us |
Bugging
What kinds of bugs are available? How are they put in place? Detected? Designed to avoid detection? What about tuning in on the computer down the block to learn the secrets it contains? Bugging typewriters? Bouncing laser beams against window panes? The Veil of Secrecy
Nobody wants to talk about bugs. The Central Intelligence Agency and National Security Agency refused to be interviewed. Private companies were also wary; several prospective sources hung up when they learned why we were calling.
Most manufacturers of bugs make it clear that they will not talk for publication. For example, Intelligence Devices Corp. of Fairfield, N.J., advertises 100 different pieces of security equipment. The ad begins, "We supply the most sophisticated electronic intelligence devices available to law enforcement, but law prohibits us from discussing our products in detail without the proper written requests...Complete and detailed product information is available only to authorized agencies upon written request on departmental letterhead."
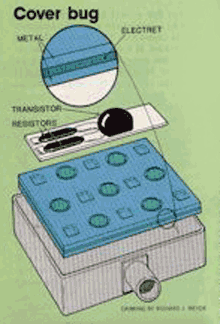
Because of the sensitive nature of the subject, no one was willing to come right out and talk in detail about bugs and bugging, or even to admit to having detailed knowledge. Nevertheless, we uncovered bits and pieces and a picture began to form. Bugs - devices designed to eavesdrop surreptitiously on conversations - we learned, come in three basic forms. First are units that contain both a microphone and a small transmitter. They are hidden in a room and transmit a signal to a nearby receiver. If such a unit is tied into a power source - room electrical wiring or a telephone line, for example - it can transmit indefinitely. And the wiring may also be used to route signals from the bug to distant points. Second are microphones. Because they can be extremely small, they can be hidden almost anywhere. But they require wires - which can be smaller than a human hair - to conduct the signal to a listening post outside the room. Finally, there are passive devices, which sit silent and unobserved but which can transmit room sounds when stimulated by a radio signal from outside. More about this later. Although all bugs fall into one of these categories, they come in a variety of shapes, forms, and sizes. Private investigators who talked on the condition they not be identified told us that bugs they find are sometime built on small circuit boards, at other times they're simply strung together in little balls of wires and components that look like a tangle of spaghetti. They can be put in small cases or encapsulated in epoxy. Epoxy encapsulation is attractive, says a textbook we saw, because such bugs look like little blobs of unidentifiable substances and may not even be recognized as bugs. Incidentally, the book, Measure by Countermeasure, a Textbook on Anti-Eavesdropping, was written to train security professionals who attend the school conducted by a security company called Microlab/FXR located in Livingston, N.J. It talks about bugs, now they work, their sizes and types, and how to find and recognize them. While some bugs are homemade, others are available commercially; you can buy them from radio supply stores where they are sold as wireless microphones or baby-sitting devices. Several such devices are pictured in this article. They cost just a few dollars and transmit a signal that can be picked up by an ordinary FM radio. "Lots of people are taking Radio Shack wireless microphones and converting them," says Charles Miller, a technician with Law Enforcement Associates, Inc., of Medford, N.J. "Take the shell off, and if you're good with your hands you can make them pretty small." "You can find them advertised in the backs of magazines," says Rob Muessel, a technical service coordinator for Information Security Associates of Stamford, Conn. More sophisticated devices - legally available in this country only to law-enforcement officers - are available off the shelf in Tokyo, Hong Kong, and at the Frankfurt airport in West Germany. "In Japan they make on transmitter that's a quarter inch square and about one and one-half inches long," says Muessel.
Bugs can be very small - small enough to be built into a fountain pen or stuck into a small hole in the wall, the binding of a book, or elsewhere. Harry A. Augenblick, president of Microlab/FXR, tells of one clever design. "This is a picture-hook bug," says Augenblick, pointing to a one-inch-long, 1/4-inch-diameter spike with a picture hook on its flat end. "First you use a tool that punches a hole in a wall, then you slip the bug in. After you hang the picture back on the wall, you wouldn't know for years that somebody had changed your picture hook." Another investigator who insisted on anonymity showed us a transmitter about the size of a book of matches. "With its battery pack this one will transmit for nine days," he said. "You can throw one of these guys in a trash can and retrieve it later." How far can such bugs transmit? "A matchbook-sized device can have a range of a quarter of a mile," says Frank G. Mason, president of a Fairfield, Conn., security firm that bears his name. The variety is endless. Pictures accompanying this article show a bug that slips into a telephone handset. Picking up the handset supplies telephone line voltage to the bug, which then transmits anything said into the mouthpiece to a nearby receiver. "We once got a call from a guy who said every time he picked up his telephone his television picture went blurry," said Muessel. "We never found out what that meant because he didn't hire us. But there was probably a transmitter planted inside his phone." Similar bugs can be designed to send out signals all the time - even when the telephone is thought to be inoperative. "Wires are often put in telephones for nonexistent intercoms or speaker phones," says Mason. "So there is a spare pair of wires." If someone intent on bugging can get to a terminal board in that building, he can wire the spare pair so that the microphone in the telephone sends a voice signal to the terminal even when it is on the hook. "In government agencies where the phones must be replaced quite often," he says, "they test phones before new ones are put in and find that eight out of ten phones are 'hot on the hook'." Another astonishing fact is how easy it is to build very small - and very effective - bugs. For example, a San Francisco security expert name Hal Lipset won momentary fame some years ago as the man who had bugged a martini olive. During our research we obtained plans and directions on how to build the infamous martini-olive bug. The plans call for hollowing out opposite ends of a small copper cylinder with a lathe, then carefully mounting in the two cavities about a dozen tiny parts - transistors, resistors, capacitors - available from any electronics supply house. The instructions describe how to cut apart a standard alkaline battery and use parts of it to construct a very small battery. Finally, a disc made of foil serves as a microphone. The instructions say the unit can be made in several sizes, including one in which the finished device is approximately 1/2 inch in length and slightly less than that in diameter. It will transmit at a frequency of 600 megahertz. How do you make it look like an olive? "A case may be formed around the unit with fiberglass putty and molded to any desired shape," the instructions conclude. The antenna is disguised as a toothpick in the olive! The most interesting bug we saw was the one pictured on the cover, which falls into the second category: microphones. The bug, a miniature electret microphone, would need thin wires leading to a receiving station. That would be no problem for someone with access to the target room; we were told that the "wires" can actually be two lines of metallic paint on a wall, which are then covered by regular paint. Such an installation is almost impossible to find. Although the term electret, representing an electrostatic analogy with permanent magnets, first appeared in 1885, a practical device wasn't devised until 1925 (the drawing shows its operating principle). An electret is made by polarizing certain waxes or plastics with high voltage; one side has a strong positive charge; the opposite side of the electret material has an equally strong negative charge. An electrical potential is permanently "frozen" into the material. Practical applications of electrets for microphones became possible with the development of low-noise transistors and suitable dielectric - nonconductive - materials. Just how small bugs can be is unknown. Frequently news reports speak of "pinhead-sized" bugs. Yet there is no evidence that bugs that small really exist. It seems at least possible that they do not, and that the pinhead estimate is a result of logical confusion. The electret mike contains a tube on one side through which the sound enters. The hole is approximately the size of a pinhead. Thus it is possible that the smallest bugs are not themselves pinhead sized, but require a pinhead-sized hole in the wall through which they pick up sound. Says Mike Russell of Sherwood Communications in Southampton, Pa., "Microphones are usually found in ceilings or mid-level in the wall. They're usually behind the wall, with a tiny hole the size of a pencil point drilled through." Perhaps the most sneaky of all bugs is the passive device. It first came to light some years ago when American security experts revealed that they were worried about low-level microwaves beamed by the Soviets at the American embassy in Moscow. Now they're reasonably sure that these were aimed at mysterious cavities built into the structures of the buildings. Steel reinforcing rods or small cone-shaped metal cavities can be hidden in the walls during construction. Sound waves within the room cause the walls to vibrate slightly, distorting these metal structures. If a microwave beam at a critical frequency is aimed at such a device, the reflected signal is slightly modulated by the sound vibrations. Careful analysis of the returning reflections can re-create the original voice signals that caused the vibration. Perhaps the most advanced - and talked about - technique of all is bouncing a laser beam off a window. The window pane vibrates slightly from the sound pressure generated by the conversation inside. The returning laser beam is modulated by these vibrations, and the original voice signals are recovered. One of the textbooks designed to train security personal contains a section on such devices. It says one can be built using a General Electric H1A1 laser, which radiates about 35 watts of power in the infrared band. It is pulsed with a simple transistor circuit at 10 kilohertz. The receiver is an astronomical reflecting telescope bought from Edmund Scientific Company. A photomultiplier tube, which turns the pulsed infrared signal into a series of electrical pulses, is mounted in place of the eyepiece. The output of the photomultiplier is then fed to an amplifier to recover the voice signal from within the room. It is questionable just how effective this technique is. Richard Heffernan, vice president of Information Security Associates says the technique probably doesn't work too well. He points out that the window pane also vibrates from passing traffic and random noise, and picking out the relatively low-level voice signals would be difficult. Other experts point out that filtering techniques have been developed to get clear pictures out of TV signals returning from space - signals that when they were received are buried in and obscured by noise. Such processing might dig voices out of the background noise. Cleaning Up the PremisesWhile companies are reluctant to talk about bugging, they're often happy to talk about their anti-bugging activities, which are legal, and which, indirectly, reveal a good bit about bugs, too. For example, Microlab/FXR's Augenblick gave Associate Editor Naomi Freundlich a demonstration of the company's SuperScout - a $25,000 bug detector the company says is used daily by 53 lesser world governments and hundreds of Fortune 500 companies.
"It looks like a cross between a vacuum cleaner and a beach-variety metal detector," she reports. "The body of the device is a briefcase-sized receiver, and attached by long electrical cords is an adjustable boom with a flat vacuum cleaner-like head on its end that functions as an antenna. Augenblick slung it over his shoulder. " 'We will find your little tape recorder whether it's on or off or even if you take the batteries out of it,' he promised. Moments before, out of his presence, I had hidden it on the lower shelf of the office coffee table under a stack of magazines. "He switched on the detection device, a nonlinear junction detector. Augenblick had explained the operating principle earlier. 'Normally if I sent a signal out around this room, it would bounce off everything and the signals coming back would all have the same frequency as the one that went out,' he said. 'But semiconductors such as transistors and diodes are nonlinear devices in which current flows more readily in one direction than in the other. That means that when SuperScout transmits at exactly one gigahertz, any semiconductor nearby will generate harmonics - that is, it will send back signals in exact multiples of the original frequency - one, two, and three gigahertz, for example.' "He methodically swept the head of the antenna up and down the office walls, across book shelves, over furniture, and finally across the floor - all the while keeping an eye on the needle at the top of the shoulder-slung portion of the device. "Then he began sweeping over the coffee table. The monitor needle swung to the right and he grinned. 'There it is!' he exclaimed triumphantly. "Nonlinear junction detectors can be misled - especially if electronic equipment containing semiconductors is anywhere nearby. 'In the beginning we did some very crude things,' said Augenblick. 'An operator conducting a sweep of former Israeli Prime Minister Golda Meir's office literally tore down her office wall and found nothing. There was just a simple radio in the next room.' " Although a nonlinear junction detector such as the one Augenblick demonstrated can find just about any bug containing semiconductors if used with sufficient care, it is expensive and tedious to use. Thus many persons debugging a site use a device called a scanner, which detects RF signals from bugs instead of the circuits inside the bug. Naomi Freundlich saw one in action at Information Security Associates in Connecticut. She reports: "Rob Muessel turned a knob on the VCR-sized receiver; at each click he homed in on radio-frequency signals. 'This instrument can scan signals from twenty kilohertz to a thousand megahertz - one gigahertz - and up into the seven- to eight-gigahertz microwave range,' he said. At one point the scanner screen danced with a whole mountain range of blue peaks, stronger than any we had seen yet. 'What are you picking up now?' I asked excitedly, imagining us picking up secret transmitted conversations. Muessel turned some dials and a particularly large peak appeared on the screen. But instead of satisfying my voyeuristic tendencies, strains of Simon and Garfunkel's song 'The Boxer' came through. We had stumbled across the FM mountain range. " 'That's all that's really involved in using this device,' said Muessel. 'You just tune through and listen.' Tuning through and zeroing in on some of the larger peaks, we picked up ham radio, cellular telephones, and even the repetitive staccato sound of transmitted data from pocket pagers. "Then Muessel set up a transmitter in the room. Even when there was no sound in the room there was a peak on the scanner screen. 'We sometimes use a steady sound source,' said Muessel as he turned on a high-pitched beeper. As the transmitter signal pulsed like a heart beat in time with the beeper I heard the regular sound in my earphones. I also listened as we picked up the same pulsating peak at exactly two and four times the frequency of the original. "The RF scanner can also be used to detect hidden video cameras. 'If we had a closed-circuit TV monitor, we could hook up a television receiver and display video signals.' said Muessel as we passed a large peak from a nearby TV station." As this demonstration illustrates, bugs that transmit continuously have a serious weakness. They're relatively easy to detect. Several ingenious schemes have been developed to minimize that possibility. For example, bugs can be built to collect information and transmit it in practically undetectable short bursts. One source speculates that such a bug could collect information in digital form for perhaps 15 seconds, then send out the whole package in one microsecond. Such a device would be practically impossible to find with a scanner. Others come with voice-actuated circuits that turn them on when there are sounds of voices in the room, off when not. Some have remote switches by which they can be turned on and off. "I can put a bug someplace and turn it on and off remotely." Miller says. "I hear you come into the room, and if I have any idea that you're going to start checking for bugs, click, it's off." All these methods help prevent detection by scanners that look for signals being radiated. Yet other bugs use a technique known as "snuggling" to avoid detection. The designer has it transmit at a frequency just barely different from a local TV station's, for example. Because its signal tends to be lost in the much more powerful TV signal, it may go undetected. Other bugs are frequency switchers. They transmit at one frequency for a few thousandths of a second, then change to another, and the another. Active bugs can often be detected by nonlinear junction detectors or scanners. These methods, however, will notdetect microphones, which neither contain semiconductors nor put out an RF signal. "You can find them" says Frank Mason, "by x-raying the walls inch by inch, but that's time-consuming, expensive, and hazardous to your health. The only other defense is physical inspection such as looking for pinholes in walls" An even more difficult-to-detect setup can be created by using a hairlike optical fiber to transmit the signal out of the room and perhaps out of the building. Because the signal is in the form of light, it creates no electromagnetic signal that can be detected, nor is it detectable by normal sweeping methods. Bugs of many types - both transmitters and microphones - are widely used, and, according to the Microlab textbook, easily placed. The book says that Microlab never identifies its clients, what it did for them, or what it found. However, it says, the company knows of actual cases of bugging detected by others. In one case, it says, one company wanted to find out what progress a competitor was making in research. So while a member of the bugging company visited the office of the director of research at the rival company, he noted the title of a book in the office. He then bought an identical book and had it fitted with a 520-kilohertz bug. The bug, made into a thin strip and sealed in epoxy, was glued into the binding of the book. Then a maintenance worker was persuaded to substitute the bugged book for the original one. The sneaky competitors parked in a car nearby and tuned in on conversations in the research director's office. In another case a financial operator widely known for sending flowers to his friends and acquaintances sent a bouquet to a legal firm reviewing a company's financial disclosure statement. In the flowers he planted a small commercially available wireless transmitter, tuned in to the conversations, and was able to make a profitable investment prior to the release of the financial statement. Sometimes planting a bug turns out to be a really inside job. In February 1982 the manager of the Soviet airline in Indonesia was arrested for running a spy ring. While he was in custody, authorities became suspicious about a scar on his chest, which he said was from an operation. But a closer look showed that a bug had been planted in the man's chest so KGB agents nearby could hear all conversation around him. Computer Bugging
Bugs have got most of the headlines in recent months, but sleuths use a lot of other high-tech tricks. One active area: eavesdropping on the sensitive information in somebody else's computer. Computer users were recently shocked to learn that it isn't even necessary for someone to have access to their premises. He can tune in to a computer from down the street. it isn't even difficult or expensive. Low-Tech BuggingBugging unprotected computers is relatively easy because it does not require access to the premises. But even typewriters can be bugged with a little effort. For example, in March 1985 U.S. officials announced angrily that the Russians had planted a large number of bugged typewriters in the U.S. embassy. Apparently they had either planted bugs in the IBM Selectrics during their shipment to the embassy or had exchanged them for pre-bugged models. How do you bug a typewriter? To find out, Senior Editor John Free visited Ace Typewriter Sales & Repair Company's shop in New York. He reports: The Cold (Bugging) WarThese and many other kinds of bugging devices were obviously used in the new U.S. embassy in Moscow. But it's been hard to tell what; in their outrage U.S. officials shed a lot of heat but little light over exactly what they had discovered. They charged that the entire building might have to be demolished, so packed is it with spy devices that they can probably never all be found and destroyed. Yet putting together the background information, it's possible to deduce what must have happened. |
|||||||||||||||||||||||
 The object to the right is a bug - a tiny microphone that can be hidden almost anywhere. It is but one in a startling arsenal of devices used today to spy on personal enemies, competing companies, and other world powers. Such devices played a major role in the recent spying controversy between the United States and the Soviet Union. Much was written about the resulting international skirmishing. But little has been said about the devices themselves, their incredible capabilities, and the astonishing technology on which they are based. Almost nothing has been written about how some of the most interesting equipment works.
The object to the right is a bug - a tiny microphone that can be hidden almost anywhere. It is but one in a startling arsenal of devices used today to spy on personal enemies, competing companies, and other world powers. Such devices played a major role in the recent spying controversy between the United States and the Soviet Union. Much was written about the resulting international skirmishing. But little has been said about the devices themselves, their incredible capabilities, and the astonishing technology on which they are based. Almost nothing has been written about how some of the most interesting equipment works. Most of this information is classified. Yet much can be learned. Today, snooping is big business with widespread industrial and commercial applications. Companies make and sell a remarkable variety of devices.
Most of this information is classified. Yet much can be learned. Today, snooping is big business with widespread industrial and commercial applications. Companies make and sell a remarkable variety of devices.